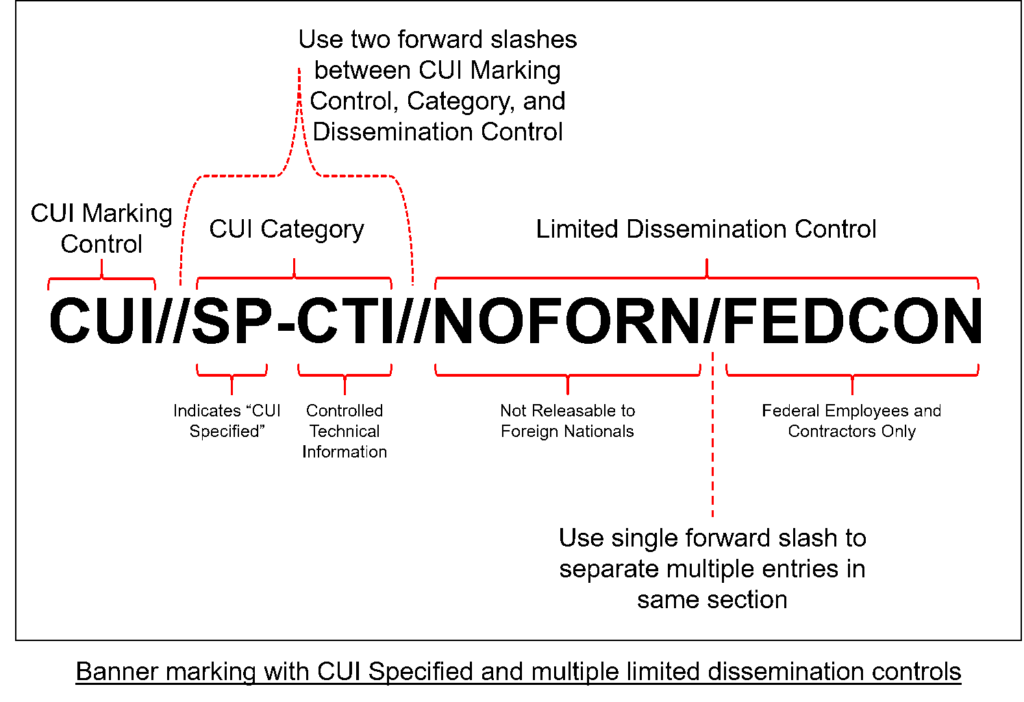
In today’s information-driven world, understanding the nuances of controlled unclassified information (CUI) is more crucial than ever. What exactly does CUI encompass? You might be surprised to learn that it includes a range of sensitive data not classified but still requiring protection.
Overview of Controlled Unclassified Information (CUI)
Controlled unclassified information, or CUI, consists of sensitive data that requires protection but doesn’t meet the criteria for classified information. Understanding CUI is vital in safeguarding national security and privacy.
Definition and Importance
CUI encompasses a variety of information types crucial to government operations. Examples include:
- Personal Identifiable Information (PII): Data that can identify an individual, such as Social Security numbers.
- Financial Data: Information related to government contracts or funding allocations.
- Proprietary Business Information: Sensitive details about company operations shared with the government.
Protecting CUI ensures compliance with regulations and prevents unauthorized access. Organizations handling this type of information maintain trust and uphold their responsibilities.
Regulatory Framework
The regulatory framework for CUI stems from federal guidelines. The National Archives and Records Administration (NARA) oversees the implementation of these standards. Key components include:
- Executive Order 13556: Establishes a uniform policy for managing CUI across federal agencies.
- CUI Program: Provides specific categories and subcategories for better classification.
Adhering to this framework helps organizations avoid penalties associated with mishandling sensitive data. It’s essential to regularly review policies and training regarding CUI management.
Categories of Controlled Unclassified Information
CUI encompasses various categories that require specific handling and protection. Understanding these categories helps you identify what information needs safeguarding.
Characteristics of CUI
CUI has distinct characteristics that set it apart from classified information. CUI is sensitive but unclassified, meaning it can’t be disclosed without proper authorization. It often includes data that, if released, could compromise privacy or national security. Furthermore, CUI is subject to federal regulations, ensuring its protection aligns with established guidelines.
Examples of CUI Types
Here are several examples of CUI types you might encounter:
- Personally Identifiable Information (PII): Includes names, addresses, Social Security numbers, and phone numbers.
- Financial Data: Encompasses government contract details, budgetary allocations, and payment information.
- Proprietary Business Information: Covers trade secrets and sensitive business plans relevant to government contracts.
- Health Records: Involves medical histories or health-related data pertaining to individuals associated with government programs.
- Law Enforcement Data: Includes investigative reports and sensitive operational details related to law enforcement activities.
Each category necessitates careful management to prevent unauthorized access or disclosure.
Specific Examples of CUI
Understanding the specific examples of controlled unclassified information (CUI) helps you identify what needs protection. Different categories of CUI include security-related, privacy-related, and proprietary business information.
Security-Related Information
Security-related information includes data that impacts national security but isn’t classified. Examples are:
- Sensitive law enforcement data: This includes details on ongoing investigations or methods used by law enforcement agencies.
- Critical infrastructure information: Data related to the safety and security of key facilities, like power plants or transportation systems.
- Emergency response plans: Documents outlining responses to various emergencies, essential for maintaining public safety.
Privacy-Related Information
Privacy-related information focuses on individual personal data that requires confidentiality. Notable examples include:
- Personally identifiable information (PII): Names, social security numbers, and addresses fall under this category and require strict handling.
- Medical records: Health-related data about individuals must be protected to ensure patient confidentiality.
- Financial details: Information regarding bank accounts or credit card numbers that can lead to identity theft if disclosed.
Proprietary Business Information
Proprietary business information consists of sensitive corporate data crucial for competitive advantage. Key examples encompass:
- Trade secrets: Formulas, practices, processes, or designs unique to a company must remain confidential.
- Contractual agreements: Terms and conditions between government agencies and private contractors need safeguarding from public exposure.
- Research and development data: Innovative ideas or projects in progress should not be shared without authorization to protect intellectual property.
Recognizing these examples enables organizations to implement proper controls around CUI effectively.
Application and Compliance
Understanding how to apply compliance measures around controlled unclassified information (CUI) is essential. You must identify CUI accurately and handle it according to established guidelines to protect sensitive data effectively.
Steps for Identifying CUI
Identifying CUI involves several clear steps:
- Review Documentation: Examine contracts, policies, or other documents for any references to CUI.
- Conduct Training: Ensure employees understand what constitutes CUI through regular training sessions.
- Assess Data Types: Evaluate the types of data your organization handles, such as PII or proprietary business information.
- Implement Classification Tools: Utilize software tools designed to identify and classify sensitive information automatically.
By following these steps, you can ensure that all forms of CUI are recognized and appropriately safeguarded.
Best Practices for Handling CUI
Handling CUI requires adherence to best practices that promote security and compliance:
- Limit Access: Grant access only to individuals who require it for their job functions.
- Encrypt Sensitive Data: Use encryption methods when storing or transmitting CUI to prevent unauthorized access.
- Regular Audits: Conduct periodic audits of your systems and processes related to the handling of CUI.
- Incident Response Plan: Develop a plan detailing procedures for addressing potential breaches involving CUI.
Adopting these practices helps maintain the integrity of sensitive information while ensuring compliance with regulations governing its protection.